Antwort How do I scan all ports in Linux? Weitere Antworten – How to do port scan in Linux
Port scanning in Linux involves using network scanning tools like Nmap, Zenmap, Netcap, and Unicornscan to identify open ports on a target system. TCP scanning utilizes techniques, such as SYN scanning, TCP Connect scanning, and FIN scanning, to determine the status of ports on a target system.Scanning specific port ranges
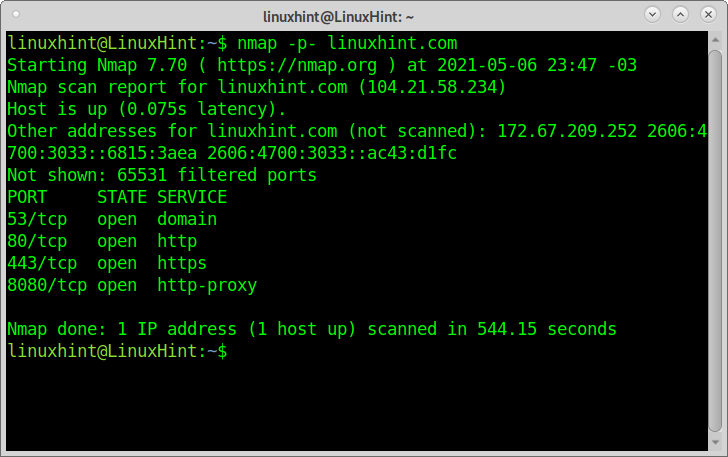
There are several ways of using the Nmap -p option: Port list separated by commas: $ nmap -p80,443 localhost. Port range denoted with hyphens: $ nmap -p1-100 localhost. Alias for all ports from 1 to 65535: # nmap -p- localhost.So you can specify -p- to scan ports from 1 through 65535. Scanning port zero is allowed if you specify it explicitly. For IP protocol scanning ( -sO ), this option specifies the protocol numbers you wish to scan for (0–255).
What is the command to scan all ports : The Nmap command you will need to scan all ports is “nmap –p– 192.168. 0.1,” which scans ports 0 through 65,535. If you want to scan a single port, the command to enter is “nmap -p 22 192.168. 1.1.” For scanning a range of ports, you would need to insert the following command in the Nmap window: “nmap -p 1-100 192.168.
What is Portscan in Linux
A port scanner is an application which is made to probe a host or server to identify open ports. Bad actors can use port scanners to exploit vulnerabilities by finding network services running on a host.
How to scan all TCP ports with Nmap : -p0- asks Nmap to scan every possible TCP port, -v asks Nmap to be verbose about it, -A enables aggressive tests such as remote OS detection, service/version detection, and the Nmap Scripting Engine (NSE). Finally, -T4 enables a more aggressive timing policy to speed up the scan.
-p0- asks Nmap to scan every possible TCP port, -v asks Nmap to be verbose about it, -A enables aggressive tests such as remote OS detection, service/version detection, and the Nmap Scripting Engine (NSE). Finally, -T4 enables a more aggressive timing policy to speed up the scan.
By default, Nmap scans the 1,000 most popular ports of each protocol it is asked to scan. Alternatively, you can specify the -F (fast) option to scan only the 100 most common ports in each protocol or –top-ports to specify an arbitrary number of ports to scan.
How to use Nmap for port scanning
Getting Started With Nmap
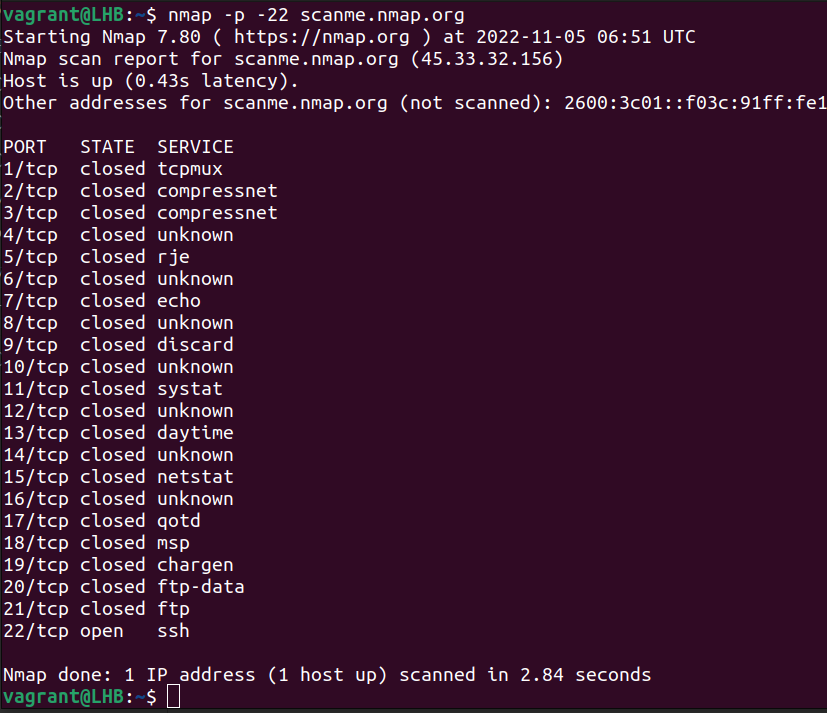
First, fire up your command line or GUI. Typing scanme.nmap.org will perform a default scan for open ports on the domain name scanme.nmap.org. Nmap provides this server to test out different scans. If you want to scan something else, type in the device's DNS name or IP address.Scan for every TCP and UDP open port: sudo nmap -n -PN -sT -sU -p- scanme.nmap.org.Check Ports via nc Command
The nc command in Linux allows users to control the netcat utility. netcat can scan the ports on local and remote systems and provide information on whether the ports are open, closed, or filtered by a firewall. Note: In CentOS, RHEL, and Debian the natcat command is ncat .
Fundamentally, it is not a crime to conduct a port scan in the United States or the European Union. This means that it isn't criminalized at the state, federal, or local levels. However, the issue of consent can still cause legal problems for unauthorized port scans and vulnerability scans.
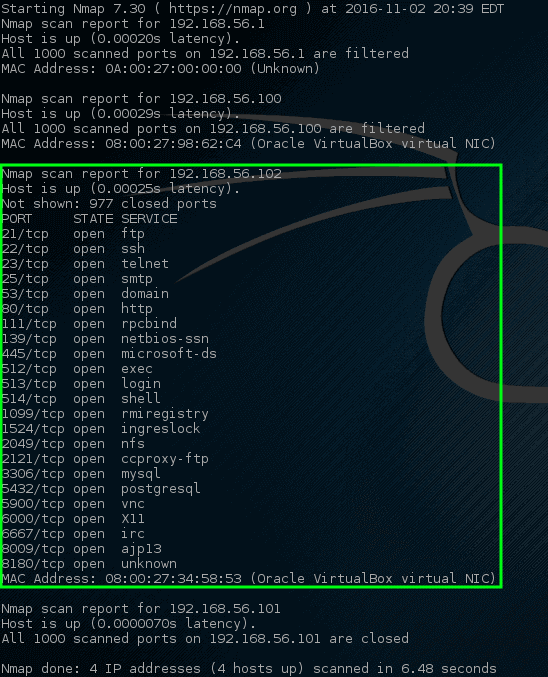
How to scan 1000 ports in Nmap : The simple command nmap <target> scans 1,000 TCP ports on the host <target> . While many port scanners have traditionally lumped all ports into the open or closed states, Nmap is much more granular. It divides ports into six states: open , closed , filtered , unfiltered , open|filtered , or closed|filtered .
How to scan all ports in Nmap : -p0- asks Nmap to scan every possible TCP port, -v asks Nmap to be verbose about it, -A enables aggressive tests such as remote OS detection, service/version detection, and the Nmap Scripting Engine (NSE). Finally, -T4 enables a more aggressive timing policy to speed up the scan.
Is it illegal to scan with Nmap
Network probing or port scanning tools are only permitted when used in conjunction with a residential home network, or if explicitly authorized by the destination host and/or network. Unauthorized port scanning, for any reason, is strictly prohibited.
The normal port ( -p ) option is used to select protocol numbers. Or you can use -F to scan all protocols listed in the nmap-protocols database. By default, Nmap scans all 256 possible values.Use the netstat command to list all open ports, including TCP and UDP, which are the most common protocols for packet transmission in the network layer. This will print: all listening sockets ( -l ) the port number ( -n )
How do I check all ports open on my IP : For Windows:
- Open the Command Prompt.
- Enter the command "ipconfig".
- Execute the command "netstat -a" to view a list of all port numbers.