Antwort How would tell Nmap to scan all ports? Weitere Antworten – How would you tell Nmap to scan all ports
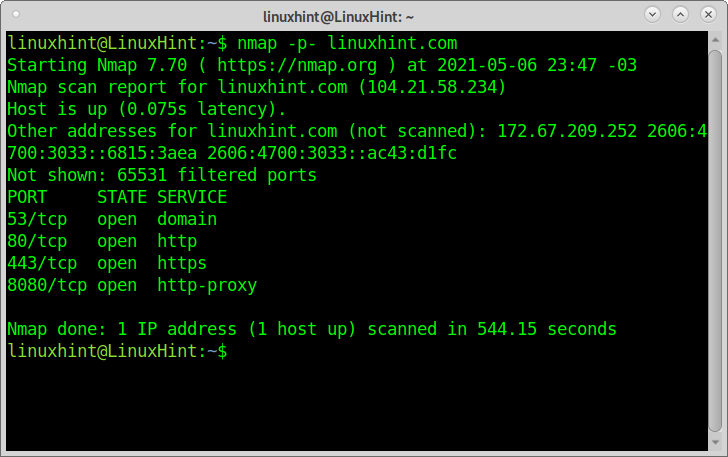
-p0- asks Nmap to scan every possible TCP port, -v asks Nmap to be verbose about it, -A enables aggressive tests such as remote OS detection, service/version detection, and the Nmap Scripting Engine (NSE).So you can specify -p- to scan ports from 1 through 65535. Scanning port zero is allowed if you specify it explicitly. For IP protocol scanning ( -sO ), this option specifies the protocol numbers you wish to scan for (0–255).The normal port ( -p ) option is used to select protocol numbers. Or you can use -F to scan all protocols listed in the nmap-protocols database. By default, Nmap scans all 256 possible values.

How to scan all ports in Linux : Check Ports via nc Command
The nc command in Linux allows users to control the netcat utility. netcat can scan the ports on local and remote systems and provide information on whether the ports are open, closed, or filtered by a firewall. Note: In CentOS, RHEL, and Debian the natcat command is ncat .
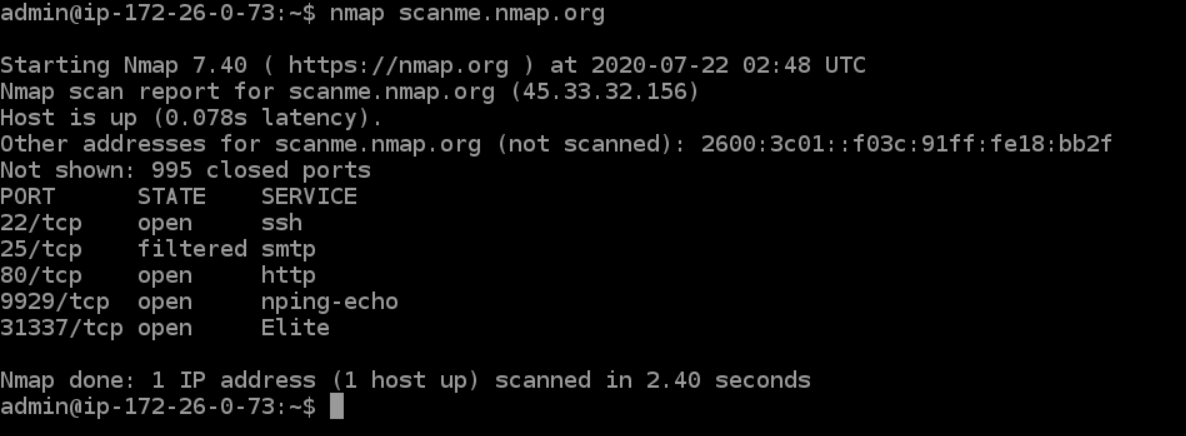
How to scan all TCP and UDP ports with Nmap
Fortunately, Nmap can help inventory UDP ports. UDP scan is activated with the -sU option. It can be combined with a TCP scan type such as SYN scan ( -sS ) to check both protocols during the same run. UDP scan works by sending a UDP packet to every targeted port.
How to scan all UDP ports with Nmap : To begin an Nmap UDP scan, the easiest way we can do this is with the -sU flag without any other options. This will scan the top 1000 UDP ports. Nmap will need sudo privileges to run a UDP scan to send custom packets.
How to check for open ports on Windows
- Open the Command Prompt.
- Type “netstat -aon” and hit enter.
- Look for the port numbers in the LISTening state.
- If the port numbers aren't in the LISTening state, you'll need to open them manually.
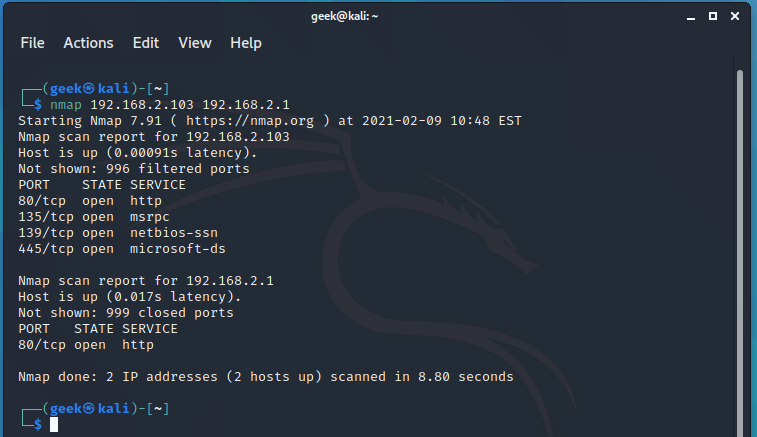
The simple command nmap <target> scans 1,000 TCP ports on the host <target> . While many port scanners have traditionally lumped all ports into the open or closed states, Nmap is much more granular. It divides ports into six states: open , closed , filtered , unfiltered , open|filtered , or closed|filtered .
How do I scan all 65535 ports in Nmap
Scanning specific port ranges
There are several ways of using the Nmap -p option: Port list separated by commas: $ nmap -p80,443 localhost. Port range denoted with hyphens: $ nmap -p1-100 localhost. Alias for all ports from 1 to 65535: # nmap -p- localhost.Sometimes you wish to scan a whole network of adjacent hosts. For this, Nmap supports CIDR-style addressing.If you would like to test ports on your computer, use the Windows command prompt and the CMD command netstat -ano. Windows will show you all currently existing network connections via open ports or open, listening ports that are currently not establishing a connection.
Scanning specific port ranges
There are several ways of using the Nmap -p option: Port list separated by commas: $ nmap -p80,443 localhost. Port range denoted with hyphens: $ nmap -p1-100 localhost. Alias for all ports from 1 to 65535: # nmap -p- localhost.
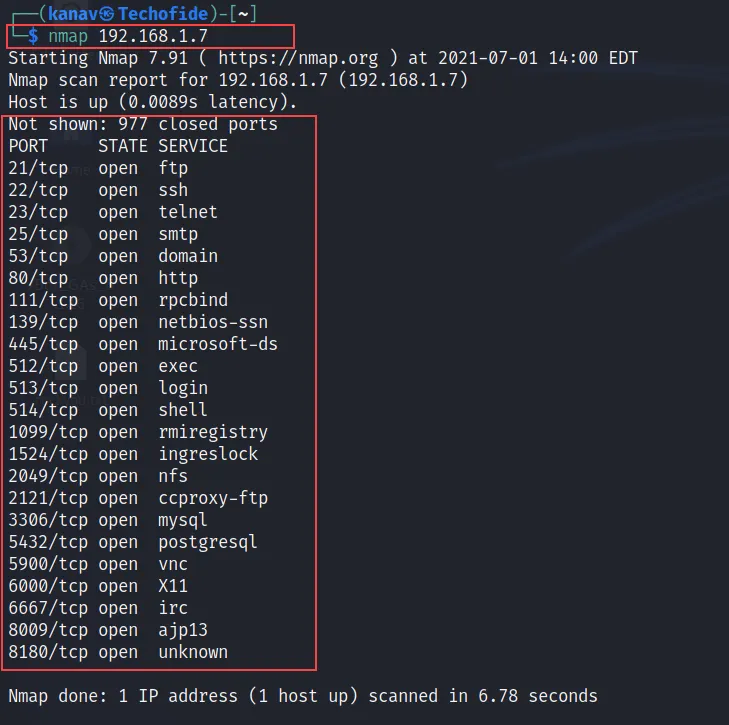
How do I scan top 100 ports : Alternatively, you can specify the -F (fast) option to scan only the 100 most common ports in each protocol or –top-ports to specify an arbitrary number of ports to scan. When none of these canned port sets suit your needs, an arbitrary list of port numbers can be specified on the command-line with the -p option.
Are Nmap scans illegal : Unauthorized port scanning, for any reason, is strictly prohibited.
How to check all ports using cmd
To find open ports on a computer and to check what application is using specified port, use the netstat command line: Open the command prompt (Start > Run > cmd) and use netstat -ano | find /i "<port_number>". It will show you all processes that use the specified port.
Scanning specific port ranges
There are several ways of using the Nmap -p option: Port list separated by commas: $ nmap -p80,443 localhost. Port range denoted with hyphens: $ nmap -p1-100 localhost. Alias for all ports from 1 to 65535: # nmap -p- localhost.Inexperienced hackers will often use the default settings of Nmap and end up getting their IP blocked by the target IDS or their packets dropped by the network firewall. An experienced hacker will be patient and probe the target using different MAC/IP addresses to gain information about the targets system.
Do hackers use Nmap : Nmap is a powerful tool for ethical hackers who want to scan and analyze network traffic and logs. It can help you discover hosts, ports, services, vulnerabilities, and other information about your target network. But like any tool, it has its advantages and disadvantages.



